TL;DR Summary
-
AI in cybersecurity in 2025 brings both unprecedented defensive capabilities and sophisticated attack
vectors - Machine learning models now detect zero-day exploits much faster than traditional methods
- AI-powered attacks have become autonomous, adapting in real-time to bypass security measures
- Human-AI collaboration remains critical for effective cyber defense strategies
Introduction
intelligence isn't just enhancing our defensive capabilities—it's completely rewriting the rules of digital
warfare. As organizations worldwide grapple with increasingly sophisticated cyber threats, AI in
cybersecurity 2025 represents both our greatest shield and most formidable challenge.
Consider this stark reality: cyber attacks now evolve faster than human security teams can respond.
Traditional security measures that served us well for decades crumble against AI-powered threats that
learn, adapt, and strike with surgical precision. Yet simultaneously, AI-driven defense systems offer
unprecedented protection, processing millions of threat signals in milliseconds and predicting attacks
before they materialize.
This comprehensive analysis explores how artificial intelligence is reshaping every aspect of cybersecurity,
from threat detection to incident response, and what organizations must understand to stay protected in
this new era.
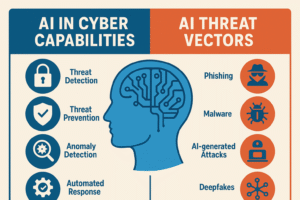
The Current State of AI-Driven Cyber Threats
Autonomous Attack Systems
systems. These AI-powered threats operate without human intervention, continuously probing networks
for vulnerabilities while adapting their tactics based on defensive responses.
Modern AI attackers employ reinforcement learning algorithms that treat network penetration like a
complex game. Each failed attempt teaches the system new patterns, making subsequent attacks
exponentially more sophisticated.
These systems particularly excel at:
- Identifying previously unknown vulnerabilities through pattern analysis
- Crafting personalized social engineering campaigns
- Coordinating distributed attacks across multiple vectors
- Evading detection by mimicking legitimate user behavior
Deepfake-Enhanced Social Engineering
Cybercriminals now deploy AI-generated voice and video impersonations that are virtually
indistinguishable from authentic communications.
In 2025, we're witnessing "vishing" (voice phishing) attacks where AI perfectly replicates executives'
speech patterns, intonations, and even breathing patterns. These attacks have successfully bypassed
voice authentication systems and convinced employees to transfer millions in corporate funds.
The sophistication extends beyond voice. Real-time video deepfakes enable attackers to conduct
convincing video calls, complete with accurate facial expressions and environmental backgrounds
scraped from social media. Traditional verification methods have become obsolete, forcing organizations
to implement multi-layered authentication protocols.
Polymorphic Malware Evolution
avoid detection. Unlike traditional malware with fixed signatures, these AI-driven variants generate
unique code patterns for each infection, rendering signature-based antivirus solutions ineffective.
Machine learning algorithms enable malware to:
- Analyze target environments and customize payloads accordingly
- Predict and circumvent specific security tools
- Distribute computational tasks to avoid behavioral detection
- Self-destruct or hibernate when analysis attempts are detected
Revolutionary AI Defense Mechanisms
Predictive Threat Intelligence
in 2025. Modern systems aggregate data from millions of sources—dark web forums, vulnerability
databases, global attack patterns—processing this information through sophisticated neural networks to
predict future threats.
These predictive models achieve remarkable accuracy by identifying subtle patterns humans would never
detect. For instance, AI systems now correlate seemingly unrelated events—unusual cryptocurrency
movements, specific code repository changes, and social media chatter—to forecast targeted attacks
weeks before execution.
Leading platforms employ transformer-based architectures similar to large language models, but trained
specifically on cybersecurity data. This enables them to understand context and intent behind potential
threats, distinguishing between legitimate security research and malicious reconnaissance.
Automated Incident Response
Orchestration, Automation, and Response (SOAR) platforms in 2025 handle entire incident lifecycles
without human intervention.
When suspicious activity triggers alerts, AI systems immediately:
- Isolate affected systems from network access
- Deploy targeted patches or configuration changes
- Initiate forensic data collection
- Coordinate response across multiple security tools
- Generate detailed incident reports for human review
accuracy. However, human oversight remains crucial for high-stakes decisions and ethical considerations
that AI cannot adequately address.
Behavioral Analytics and Anomaly Detection
unsupervised learning algorithms. Modern AI systems establish baseline behavior patterns for every user,
device, and application within an organization's ecosystem.
These sophisticated models detect anomalies that would appear normal to rule-based systems:
- Subtle changes in typing patterns indicating compromised credentials
- Unusual data access patterns suggesting insider threats
- Microsecond-level network timing variations revealing man-in-the-middle attacks
- Resource utilization anomalies indicating cryptomining or data exfiltration
deadlines, team collaborations, and business cycles when evaluating anomalies, dramatically reducing
false positives that plagued earlier generations.
Industry-Specific Applications
Financial Services Protection
sophisticated fraud while maintaining seamless customer experiences. Banks and fintech companies
deploy AI across multiple fronts:
Real-time transaction monitoring uses deep learning to identify fraudulent patterns across millions of
daily transactions. These systems analyze hundreds of variables—transaction amounts, merchant
categories, geographic locations, device fingerprints—making split-second decisions with very high
accuracy.
AI also powers next-generation authentication systems combining biometric data, behavioral patterns,
and contextual information. Customers experience frictionless access while attackers face insurmountable
barriers, even with stolen credentials.
Healthcare System Defense
AI-powered attacks. In response, the sector has adopted specialized AI defenses tailored to medical
environments.
AI systems now monitor medical device networks, detecting anomalies that could indicate ransomware
attempting to compromise critical equipment. Machine learning models trained on healthcare-specific
data recognize patterns unique to medical workflows, distinguishing between legitimate emergency
access and potential breaches.
Protected health information (PHI) receives additional safeguards through AI-powered data loss
prevention systems that understand medical terminology and context, preventing unauthorized
disclosure while allowing necessary information sharing for patient care.
Critical Infrastructure Security
Power grids, water systems, and transportation networks employ industrial AI security solutions designed
for operational technology (OT) environments. These systems must balance security with operational
continuity, as false positives could trigger unnecessary shutdowns.
AI models trained on industrial control system (ICS) protocols detect subtle manipulations that could
indicate nation-state attacks or sabotage attempts. Department of Homeland Security guidelines on AI
implementation for critical infrastructure protection (link) provides frameworks for deploying these technologies
while maintaining safety and reliability.
Implementation Challenges and Solutions
Data Quality and Model Training
Organizations struggle with several challenges:
Insufficient historical attack data limits model accuracy, particularly for novel threat types. Many
companies lack the volume of security events needed to train robust models, leading to high false
positive rates or missed detections.
Solutions emerging in 2025 include:
-
Federated learning approaches allowing organizations to benefit from collective intelligence without
sharing sensitive data - Synthetic attack data generation using generative AI to supplement real-world datasets
- Transfer learning techniques adapting pre-trained models to specific organizational contexts
- Industry-specific threat intelligence sharing platforms
Integration Complexity
systems often lack the APIs and data formats required for AI integration, while modern tools may conflict
with established security policies.
Successful implementations follow structured approaches:
- Conducting comprehensive infrastructure assessments before AI deployment
- Implementing middleware layers to bridge compatibility gaps
- Adopting gradual rollout strategies with extensive testing phases
- Establishing clear governance frameworks for AI decision-making
Skills Gap and Workforce Adaptation
professionals need understanding of machine learning concepts, while data scientists require
cybersecurity domain knowledge.
Organizations address this gap through:
- Comprehensive training programs combining AI and security curricula
- Hybrid teams pairing security analysts with data scientists
- AI-assisted tools that abstract complex ML operations
- Partnerships with academic institutions and specialized vendors
Ethical Considerations and Privacy Concerns
Surveillance and Privacy Balance
that monitor employee behavior, even for legitimate threat detection, create surveillance environments
that may violate privacy expectations.
Organizations must navigate complex ethical territories:
- Defining acceptable monitoring boundaries
- Ensuring transparency about AI surveillance capabilities
- Implementing privacy-preserving techniques like differential privacy
- Establishing clear data retention and deletion policies
Algorithmic Bias in Security Decisions
flag legitimate activities from certain user groups as suspicious based on historical patterns, creating
discriminatory outcomes.
Addressing bias requires:
- Diverse training datasets representing all user populations
- Regular auditing of AI decisions for discriminatory patterns
- Human review processes for high-impact security decisions
- Transparent documentation of model limitations and potential biases
Accountability and Decision Authority
incident responses—determining accountability becomes challenging. Organizations must establish clear
frameworks defining when AI can act autonomously versus requiring human approval.
Future Outlook: What's Next for AI in Cybersecurity
Quantum-Resistant AI Security
address quantum threats. Research in 2025 focuses on developing AI models that can detect and defend
against quantum-enhanced attacks while preparing for post-quantum cryptography transitions.
Explainable AI for Security Operations
The black-box nature of many AI models creates challenges in security contexts where understanding
decision rationale is crucial. Next-generation systems emphasize explainability, providing clear reasoning
for security alerts and actions.
NIST framework for explainable AI in cybersecurity applications (link) outlines
standards ensuring AI security decisions remain auditable and comprehensible.
Collaborative Defense Networks
systems from different organizations share threat intelligence in real-time. These networks will enable
collective defense against sophisticated attackers while preserving organizational autonomy and
confidentiality.
Best Practices for Organizations
Strategic Implementation Roadmap
- 1: Assessment Phase: Evaluate current security posture and identify AI opportunity areas
- 2: Pilot Programs: Start with limited deployments in controlled environments
- 3: Gradual Expansion: Scale successful implementations while maintaining oversight
- 4: Continuous Optimization: Refine models based on real-world performance
- 5: Full Integration: Achieve seamless operation within security architecture
Vendor Selection Criteria
- Demonstrated expertise in both AI and cybersecurity domains
- Transparent model performance metrics and limitations
- Strong privacy and data protection practices
- Ability to integrate with existing security infrastructure
- Ongoing support and model updating capabilities
Measuring ROI and Effectiveness
- Mean time to detect (MTTD) and respond (MTTR) improvements
- False positive rate reductions
- Prevented incident costs
- Operational efficiency gains
- Compliance and audit performance
Frequently Asked Questions
How does AI in cybersecurity differ in 2025 compared to previous years?
predictive analysis, autonomous response, and contextual understanding. Modern AI can anticipate
attacks before they occur, adapt defenses in real-time, and coordinate complex response strategies
across entire infrastructures. The integration is deeper, with AI embedded in every security layer rather
than functioning as standalone tools.
What are the biggest AI-powered cyber threats organizations face today?
deepfake-enhanced social engineering that bypasses traditional verification, polymorphic malware that
mutates to avoid detection, and AI-powered reconnaissance that identifies vulnerabilities faster than
patches can be deployed. These threats operate at speeds and scales that overwhelm traditional security
measures.
Can smaller organizations effectively implement AI cybersecurity solutions?
specific solutions designed for smaller deployments. Many vendors offer scalable platforms with pre-
trained models that don't require extensive in-house expertise. Smaller organizations can also benefit
from shared threat intelligence networks and federated learning initiatives.
How can organizations prepare their workforce for AI-driven security operations?
advanced cybersecurity concepts. Creating hybrid teams that combine security and data science
expertise, implementing AI-assisted tools that simplify complex operations, and partnering with
educational institutions for specialized training programs are essential strategies. Regular hands-on
exercises with AI security tools help teams build practical experience.
Conclusion
fundamental paradigm shift in how we protect digital assets. We stand at a critical juncture where the
same AI technologies that empower unprecedented defensive capabilities also enable sophisticated
attacks that challenge our traditional security frameworks.
Organizations that thrive in this new landscape will be those that embrace AI not as a silver bullet, but as
a powerful tool requiring thoughtful implementation, continuous adaptation, and human oversight. The
key lies in building robust AI-enhanced defense systems while maintaining the flexibility to respond to
rapidly evolving threats.
As we've explored AI In Cybersecurity in 2025 throughout this analysis, success demands more than just
deploying AI tools. It requires comprehensive strategies addressing technical integration, workforce
development, ethical considerations, and collaborative defense approaches. The organizations that master
this balance—leveraging AI's power while acknowledging its limitations—will define the next era of
cybersecurity excellence.
The journey ahead promises continued innovation and challenge in equal measure. By understanding
both the opportunities and risks AI presents, preparing our teams for AI-augmented operations, and
maintaining vigilance against emerging threats, we can harness artificial intelligence to build more
resilient, adaptive, and effective security postures.
